The threat is not the visible monster, nor the grinding machine of conventional warfare. The true enemy is a silent, microscopic genius: the apex predator of adaptation. For too long, we viewed nature as a passive backdrop, a collection of beautiful but simple systems. But biology holds a dark truth: the parasite is the ultimate bio-engineer, capable of a terrifying sophistication that demands our immediate attention in our quest for a bio-mimetic defense against parasitic AI.
Look to the jungles, where the Ophiocordyceps fungus performs its unholy ritual. This, the infamous “zombie-ant fungus,” doesn’t merely kill its host; it completely overrides the organism’s core operating system. It compels the ant to climb to a specific, fatal height, ensuring maximum spore dispersal. Such biological zero-day exploits demonstrate the need for a bio-mimetic defense against parasitic AI. It targets the core command center and locks out the user’s free will.
The strategic mandate for human security, whether protecting our digital infrastructure or our biological integrity, is chillingly clear: We must learn to use bio-mimetic defense strategies to protect our systems from external, adaptive control.

I. The biological threat: adaptive control systems
The parasite’s success lies not in blunt force, but in elegant precision. It is a master of learning, targeting, and co-opting the host’s most vital control systems. In this context, developing a bio-mimetic defense against parasitic AI becomes crucial.
Our traditional defense systems: the firewalls, the antibiotics, the static protocols, are tragically reactive. They defend only against known threats, leaving our systems wide open to the unknown.
The Mimétique Threat demonstrated by the parasite is far more profound. It employs dynamic learning. The parasite chemically navigates the host’s body, adapting its defense-evasion in real-time until it locates the brain. It then releases compounds specifically designed to override the host’s free will. This is not a brute force attack; this is a highly targeted siege on the seat of consciousness itself. The strategic parallel is undeniable: it is the ultimate cyber attack, a biological lock-out that hands the attacker the keys to the entire system.
II. Counter adaptive systems
To defeat a genius, we must think like a genius. We must translate the parasite’s ruthless ingenuity for attack into a blueprint for defense, creating counter-adaptive systems designed for unpredictable counter-intelligence. A bio-mimetic defense against parasitic AI leverages these insights.
A. The “immune drift” defense (think internal security!)
If the parasite adapts to the host, the host must adapt to the parasite’s learning. This is the Immune Drift principle.
We must mimic the human immune system’s core principle: constant, non-linear mutation against evolving threats. In the digital realm, this means designing Adaptive Cyber-Defenses that continuously randomize their internal data architecture or shift verification pathways. This forces the attacking AI or malware to constantly re-map the system, rendering its learned pathways obsolete every 24 hours. The goal is not elimination, but exhaustion, this to maximize the attacker’s energy cost until the system becomes too expensive and unpredictable to conquer.
B. The “camouflage network” (think, organizational security!)
The secret to survival is often invisibility. The host must conceal its vital command centers from the parasitic attack.
This code demands we mimic the Chameleon’s ability to instantly control its surface appearance and the Octopus’s decentralized, brilliant nervous system. The application is Distributed Authority and Deception. We design organizational and network structures that spread control and embed “deception nodes”, entire sections of the network that are decoys. The organizational intelligence is diffused across the network, ensuring no single, centralized server or command center can be easily taken over. The parasitic attack wastes vital time and resources on non-critical assets, finding only hollow shells where the brain should be.
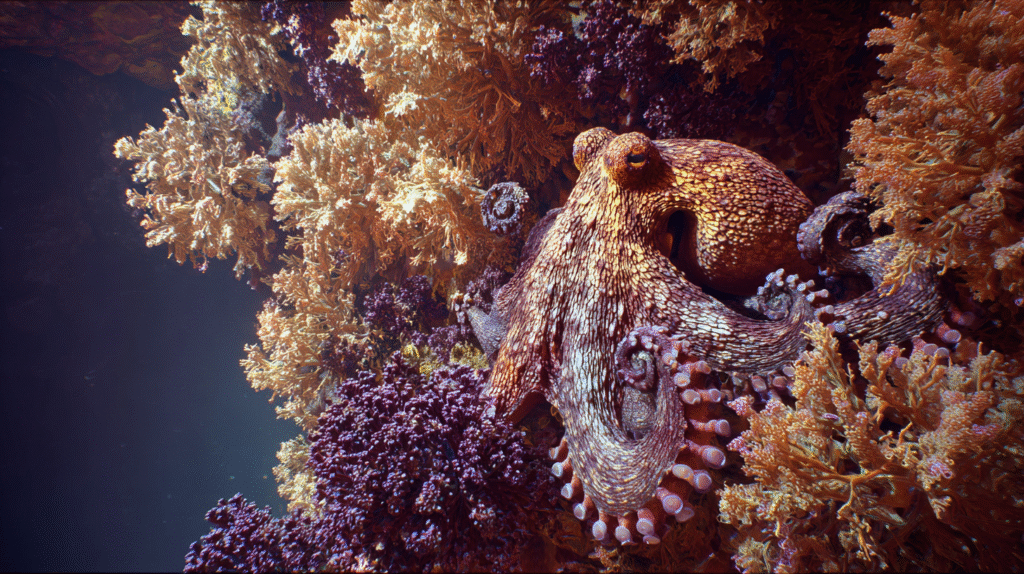
III. The cost of biological naïveté
The Zombie Code is not a fiction; it is a profound wake-up call. The threat of biological mimicry, whether it arrives as fungal spores or as synthetic malware, is that it targets the fundamentals of our existence: our autonomy, our stability, and our will.
By studying the world’s most cunning biological attackers, we gain the most powerful insights into defense. The ultimate strategic advantage lies not in building thicker walls, but in building security that is as dynamic, unpredictable, and ruthlessly adaptive as the parasitic systems that already rule the darkest corners of nature. The future of security belongs to those who learn to fight fire with the very same bio-mimetic fire to create a robust defense against parasitic AI threats.


Leave a Reply